Search the Community
Showing results for 'Self Signed certificate'.
-
Hello everyone, I use a self-signed certificate for the development environment created through openssl following unigui's own post (here). However, when running the application, any browser considers it insecure and in my case it makes the application slow. For now I disable ssl as it is only in the laboratory. Is there any way around this?
-
Hello @Abaksoft, your tip was of great help, however, in my case I don't need other devices to access the "server", just the computer itself that is compiling. So, I made a summary of the manual. 1 - Create the san.cnf file in the OpenSSL bin folder (C:\Program Files\OpenSSL-Win64\bin). The content of the file looks like this: [req] default_bits = 2048 distinguished_name = req_distinguished_name req_extensions = req_ext x509_extensions = v3_req prompt = no [req_distinguished_name] countryName = XX stateOrProvinceName = XX localityName = XXXX organizationName = XXXX commonName = 127.0.0.1: Self-signed certificate [req_ext] subjectAltName = @alt_names [v3_req] subjectAltName = @alt_names [alt_names] IP.1 =127.0.0.1 Replace the "X" with your parameters 2 - Open cmd as admin 2.1 - cd C:\Program Files\OpenSSL-Win64\bin 3 - Run command openssl genrsa -out root.key 2048 openssl req -x509 -days 3650 -new -nodes -key root.key -out root.pem -config san.cnf openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -keyout key.pem -out cert.pem -config san.cnf 4 - You created the three files (root.pem, cert.pem, Key.pem) inside the bin folder. Copy these three files to the root directory where the .exe of your unigui project is located. 5 - Finally, open the Windows certificate manager (certmgr.msc), navigate to the "trusted root certificate authorities" folder and import the cert.pem file Close browser e run project.
-

Problem with SSL Certificate implementation
Felipe Lugo replied to Felipe Lugo's topic in Deployment
Thanks Sherzod for your response. The behavior in SSL Demo using the demo certificates is the same (self-signed certificate) as when using Certificates purchased from a Certificate Authority. The installation of the certificates on my web server with its own domain, is it the IIS and/or Apache server? Thanks in advance, -
Hello, Yes, because a self-signed certificate is used. Yes...
-
Dears, You can download it here : http://forums.unigui.com/index.php?/topic/18951-help-with-ssl-intranet/&do=findComment&comment=136067
-
Yes, this is possible solution and is good practice. If the file is signed then it is not malicious! - but not always true. Digitally signed files know who the owner of the certificate is, but is there also certificate theft, even if signed it does not make the file safe. "Here in Brazil we have e-card (hard solution) to validate biz and digital signatures in docs (gov, secure transactions, banks etc) much alike a "smart" debit card" - Our government too, but that's because they want to know who owns the file and for security reasons (i think). In theory, we apply the principle: the user is malicious and we look for as many rules as possible to make it difficult for him to attack the server. Because the most dangerous thing in an attack with an infected file is the infection of the server. When a server is infected, the consequences are not just for the server owner, but also for the users. I recently read an article about an mobile phone company vulnerability that went undetected for some years. This has certainly given malicious individuals the opportunity for more attacks or data theft. Ultimately, the goal is to keep the server from getting infected. to your questions: 1- You allow the user to upload to your server with authentication provided by you - Yes, only authorized user can upload files, even I add user details in the upload process, which is verified by the server 2- You use https - Yes, not self signed 3- You can save in a non public folder with no access to browser - Yes, outer directory, protected with user rights of OS. 4- You can modify rights to such file - not yet, but in the future I will (I work on it) 5- You can save in raw format with out decoding or absolutely removing association to a app. - Yes, I save a file with a changed name and no extension. The raw format is a good idea, thanks 6- Only who upload can download it - No, only authorized user to app can download or open files. Like example : 1. I give rights to clients to upload advertisement files and this ad will be played on other users (such as video or image with iFrame) 2. I give rights to clients to upload their own image/video/other files (like YouTube) and it will play on other users 3. I grant rights to an internal user of the company to upload video files from security cameras, then only camera owners can download recordings from each day all this can be do it from mobile device (problem with smart cards) or pc 7- All upload to your server you have antivirus and such - Yes, I have an antivirus app and an anti-malware app. But getting information that files are dangerous is not enough if no one is watching (like at 03:00 in the morning) and files are on server. Consider this: a- If not sharing to third parties... issue is ? - 1. server is at risk, all work can stop. 2. I share it, so the risk is to malicious files go to clients PC and make them bot net. b- if now allowing downloads and any kind of access... issue is ? - risky files may attack clients, a Trojan horse or worm c- Any options the burden of processing and things going wrong is at the client-side (delays, corruptions etc etc). - I prefer it to be done on the server side, and on the client side only hash files and HMAC for them. On the server side, when they upload files, they first go to the temporary directory (with changed names), but they are not encrypted, and this creates a risk for the server, so I'm looking for a way to secure (obfuscate/encrypt) files beforehand.
-
Hi Abaksoft, Thanx for your PERFECT work .. i tried a lot! of things and found a solution for the Android Problem 😉 The maion problem is the "-extensions v3_req" 1. change in delphi: //A.2.2 root.pem stDays:=intToStr(365 * upYrears.Position); param:='req -x509 -days ' + stDays + ' -new -nodes -key root.key -out root.pem -config san.cnf -extensions v3_req'; ShellExecute(Application.Handle ,PChar('RunAs'),PChar(Fichier),PChar(param),PChar(Dossier),SW_HIDE); sleep(300); //A.2.3 cert.pem param:='req -x509 -nodes -days ' + stDays + ' -newkey rsa:2048 -keyout key.pem -out cert.pem -config san.cnf -extensions v3_req'; ShellExecute(Application.Handle ,PChar('RunAs'),PChar(Fichier),PChar(param),PChar(Dossier),SW_HIDE); sleep(300); 2. change in san.cnf [req] default_bits = 2048 distinguished_name = req_distinguished_name req_extensions = v3_req x509_extensions = v3_req prompt = no [req_distinguished_name] countryName = XX stateOrProvinceName = N/A localityName = N/A organizationName = Self-signed certificate commonName = Self-signed certificate [req_ext] subjectAltName = @alt_names [v3_req] subjectAltName = @alt_names basicConstraints = critical,CA:true [alt_names] IP.1 =10.0.0.10 3. Export CA in Windows - and import it as CA in Android .. Works 🙂
-
Creating a Self Signed Certificate in 3 Secondes...
Abaksoft replied to Abaksoft's topic in Sample Projects
No, it does'nt work. Self signed certificats are for testing purpose or for local network. If you want to use your domain name from web as secure https://xxxx.domain.com.br the task is hard : you have to export your certificat from your server and communicate it to all your known clients to install it on there PC / Device ! Mmm...Asking ChatGp4 "is it possible to get a free trusted certificate for a public websites ?" Answer: "Yes, it is possible to obtain a free trusted certificate for a public website. There are several certificate authorities (CAs) that offer free SSL/TLS certificates that are trusted by major browsers. Here are a few popular options: Let's Encrypt: Let's Encrypt is a non-profit CA that provides free SSL/TLS certificates. They offer an automated certificate issuance and renewal process, making it easy to obtain and manage certificates for your website. Cloudflare: Cloudflare offers a free SSL/TLS service called "Universal SSL." When you sign up for their service, they provide you with a free SSL certificate that is automatically installed on your website. Cloudflare acts as a reverse proxy, encrypting the traffic between the client and Cloudflare's servers. ZeroSSL: ZeroSSL offers free SSL certificates that are valid for 90 days. They provide both automated and manual certificate generation options. ZeroSSL also offers an ACME client that can be integrated into your server for automated certificate issuance and renewal. SSL.com: SSL.com provides a free SSL certificate option called "SSL.com FREE." Their free certificate is valid for 90 days and supports both domain validation and wildcard certificates. It's worth noting that while these free certificates are trusted by browsers, they may have some limitations compared to paid certificates. For example, they may have a shorter validity period, limited support, or fewer additional features. If your website has specific requirements or needs extended validation, you may need to consider a paid certificate from a trusted CA. Additionally, some hosting providers or content delivery networks (CDNs) also offer integrated SSL/TLS solutions with free certificates. It's worth checking if your hosting provider has any options available for obtaining trusted certificates at no additional cost." -
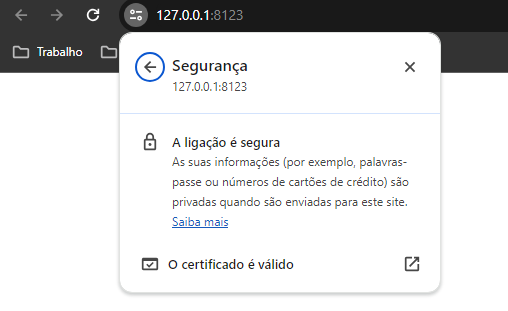
Dears, I was finally able to do something: If one day, you will have to develop an Unigui app: - Under local network, - Without Internet, - Which requires an SSL (example Scann Camera) Then read the following: I thought, wrongly to create "Self Signed Certificate". Today, most of browsers reject them. So, after 3 days search, I understood that it was necessary to use another technic : Create a localhost Certificate by mkcert This is inspired by (thx to the Author) : https://technixleo.com/create-locally-trusted-ssl-certificates-with-mkcert-on-windows OK...Step by Step : 1. Installing mkcert on Windows 1.1 mkcert can be installed by Chocolatey To install Chocolatey, you must first ensure the Policy AllSigned Open PowerShell as Admin Get-ExecutionPolicy if Restricted then : Set-ExecutionPolicy AllSigned 1.2 To install Chocolatey see https://chocolatey.org/install In PowerSehlle type (in a single line): Set-ExecutionPolicy Bypass -Scope Process -Force; [System.Net.ServicePointManager]::SecurityProtocol = [System.Net.ServicePointManager]::SecurityProtocol -bor 3072; iex((New-Object System.Net.WebClient).DownloadString('https://community.chocolatey.org/install.ps1')) 1.3 install mkcert In PowerSehlle type: choco install mkcert The mkCert Directory (by default) is: C:\Users\...\AppData\Local\mkcert 2. Generate my 2 pem files In PowerSehlle type: mkcert -install This will generate 2 files in C:\Users\...\AppData\Local\mkcert: rootCA.pem rootCA-key.pem 3. Generate a localhost.p12 Certificate In PowerSehlle type: mkcert -pkcs12 localhost This will generate localhost.p12 certificate which will be in the PowerShell directory, ie: ..\System32 4. Import the localhost Certificate Touche Win + R key: mmc File > Add > Certificates > Add Computer account local computer OK Right click / on WEB Hosting Certificates > All Tasks Machine Room Select localhost.p12 Certificate Next specify the password (default): changeit Check: Key Exportable Place of the Certificate on : Web Hosting (dépend on your windows langage : example for french : Hébergement Web) This will create 2 Certificates (in Web Hosting): - localhost - mkcert myDESKTOP-xxx 5. Project Unigui Requires 3 files: cert.pem key.pem root.pem Do not use root.pem = rootCA.pem ( C:\Users\...\AppData\Local\mkcert ) key.pem = rootCA-key.pem ( C:\Users\...\AppData\Local\mkcert ) wich are generated by mkcert. Use instead the new 3 files, obtained online (by converting the p12 file in a new global pem file) 5.1 Split localhost.p12 into 3 Files You can obtain the 3 files via a conversion of the Certificate: localhost.p12 Use Online: https://www.sslshopper.com/ssl-converter.html - Upload the Certificate File: localhost.p12 - indicate the type: PFX/PCKC#12 - Convert To: Standard PEM - Password: changeit You will get global File, containing 3 blocks : start ...end Separate them with Notebook, and save them into 3 files: The first = cert.pem The second = root.pem The third = key.pem 5.2 Compile your project and run it : https://localhost:8077/ is Secure Have fun... ___________________ PS: if you are interesting by an easy way to scan BareCode via your Android device (wich requires an SSL url) you can use Falcon Store - Components Delphi from our Friend Marlon. Very fast and light ! http://forums.unigui.com/index.php?/topic/11359-falcon-store-components-delphi-httpsstorefalconsistemascombr/#comment-60260
-
A good news 😅 Incredible ! When opening the same app protected by our Self Signed Certificat, on a Customer iphone , the secure padlock appears. Without importing certificate ! "Wow...the secure warning did'nt appear... ". I said "Well it's an iphone..." He said. It seems that : extensions v3_req' Is a good recipe.
-
In a previous topic, we saw how to create a Self Signed Certificate with mkCert and trusted it with mmc. That works fine but havy method ! Here we will see an other method much easier : OK, Step by Step : 1. install the latest OPENSSL 2. Prepare a conf file (NotePad) : [req] default_bits = 2048 distinguished_name = req_distinguished_name req_extensions = req_ext x509_extensions = v3_req prompt = no [req_distinguished_name] countryName = XX stateOrProvinceName = N/A localityName = N/A organizationName = Self-signed certificate commonName = 120.0.0.1: Self-signed certificate [req_ext] subjectAltName = @alt_names [v3_req] subjectAltName = @alt_names [alt_names] IP.1 = 192.168.1.11 2. Save it as C:\Program Files\OpenSSL-Win64\bin\san.cnf - Replace IP.1 variable by your IP adress (local machine) - if you want DNS instead of IP, replace the Section [alt_names] by : [alt_names] DNS.1 = mywebsite1.dev DNS.2 = mywebsite2.dev On a local network, without internet, mywebsite1.dev should be defined on C:\Windows\System32\drivers\etc\hosts file : 192.168.1.11 mywebsite1.dev 3. Create your 3 .pem files (like Unigui doc) but with this conf : 3.1. cmd as admin cd C:\Program Files\OpenSSL-Win64\bin openssl genrsa -out root.key 2048 openssl req -x509 -days 3650 -new -nodes -key root.key -out root.pem -config san.cnf openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -keyout key.pem -out cert.pem -config san.cnf 4. Copy the 3 .pem files C:\Program Files\OpenSSL-Win64\bin : root.pem cert.pem Key.pem near your Unigui Project.exe 5. Add the cert.pem on the Windows Trusted Root Certificates (in case of a windows server). The most important step here, wich is not indicated on the Unigui doc : (FmSoft Team, could you please add it ) Copy your cert.pem on a temporary location, example C:\cert.pem Open PowerShell as admin Type these commands : $certPath = "C:\cert.pem" $cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2($certPath) $cert.Import($certPath) $certStore = New-Object System.Security.Cryptography.X509Certificates.X509Store -ArgumentList "Root", "LocalMachine" $certStore.Open("ReadWrite") $certStore.Add($cert) $certStore.Close() This will automatically add the certificat cert.pem on the trusted root certificats zone. If you want to do it in a single ligne (1 command ), just add ; between commands line1; line2; line3;....;line7 You can verify the new certificat, by openin win + R : mmc and go to the trusted root certificates zone 6. Run your Unigui SSL Project, and you will see the black padlock protected site. Have fun
-
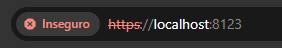
Dears, I am developping an intranet Unigui application for SuperMarket : The purpose is to Scan BarCode from manager Smartphone Camera, in real time for Inventory. As the camera requires SSL, the URL will be a classical local Server IP adress like : https://192.168.1.5:8077 ( Customer server = 192.168.1.5 ) OK, we can buy Certificate from authority or get a free one, but in this case, supermarket customers have no internet. So, it's not possible to attribute a Domaine Name in intranet https://www.mysupermarket.com So, I give up ... The solution will be a Self Signed Certificate (with IPAdress). But all browsers reject this certificate. I googled and found how to export / import for accepting Certificate, but not work with the Unigui Farshad DEMO SSL. Any idea ? Thx.
-
Hello, i'm trying to make work SSL with a test unigui application (standalone) I have generated a certificate as explaing in this link: Developer's Guide > Deployment > SSL Configuration > Generate a Self-Signed Certificate (unigui.com) I have created the certificate with a password and have inserted the password in the SSLPassword property in my application. I suppose i have done it right. Of course i have enabled ssl (ssl.enabled=true) The application is correctly executed using https://127.0.0.1:8077 but the browser tell me the the connection is not safe. Does it happens because i'm using a self-generated certificate ? Below you can see the properties of the servermodule. thanks Roberto object UniServerModule: TUniServerModule OldCreateOrder = False TempFolder = 'temp\' Title = 'New Application' SuppressErrors = [] Bindings = <> SSL.Enabled = True SSL.SSLOptions.RootCertFile = 'root.pem' SSL.SSLOptions.CertFile = 'cert.pem' SSL.SSLOptions.KeyFile = 'key.pem' SSL.SSLOptions.Method = sslvTLSv1_2 SSL.SSLOptions.SSLVersions = [sslvTLSv1_2] SSL.SSLOptions.Mode = sslmUnassigned SSL.SSLOptions.VerifyMode = [] SSL.SSLOptions.VerifyDepth = 0 SSL.SSLPassword = '050302' ConnectionFailureRecovery.ErrorMessage = 'Connection Error' ConnectionFailureRecovery.RetryMessage = 'Retrying...' Height = 150 Width = 215 end
-
Error 503 in Project with TUniCalendarPanel and SSL(IIS)
Abaksoft replied to Fernando Silva's topic in General
I tested your code and works fine with .exe + SSL (Self signed Certificate). I did'nt try it as IIS +SSL. ________ How are you adding your SSL in IIS ? -
I compiled all above in program wich create a Self Signed Certificate in 3 secondes. Best Regards... See the updated program here : http://forums.unigui.com/index.php?/topic/18951-help-with-ssl-intranet/&do=findComment&comment=141667 Prg.7z
-
Hello, Can you please clarify? First of all, were you able to generate a self-signed certificate with an IP address?
-
maybe this will help to You: I use trusted certificate. I had set up in the URL='https://X.X.X.X:8070/...'and the problem was it. After I set it up in the URL='https://myaddres:8070/...' the problem solved in MsgSrv. http://forums.unigui.com/index.php?/search/&q="Self Signed certificate"&quick=1 or this:
-
hello I downloaded my certificate (TrustCor Standard DV noip) i installed my ssl on my server which needs three cert.pem root.pem and key.pem files cert is my certificate. key.pem my private for root key I downloaded chain pem converted to rooy.pem. the chain.pem file contains 3 certificates: 1 intermediate1, intermediate2 and root all works fine on desktop pc but for android I have a problem with invalid certificate please help me the result of the test my certificate gives: Certificate #1: RSA 2048 bits (SHA256withRSA) Server Key and Certificate #1 Subject mondomaine.ly Fingerprint SHA256: 53c2a119bfe36c74e2830b4df91015f0337eeafdb75b3b29652c35ad646f7d7c Pin SHA256: LBEhUc/LINIlfK7G/C29ZpAzgV1fFegJ+HnN4g47o0w= Common names mondomaine.ly Alternative names mondomaine.ly Serial Number 00dfcea85d0ab3312a7f502442 Valid from Sun, 13 Jun 2021 08:49:16 UTC Valid until Mon, 13 Jun 2022 08:49:15 UTC (expires in 11 months and 27 days) Key RSA 2048 bits (e 65537) Weak key (Debian) No Issuer TrustCor DV SSL CA - G2 - RSA AIA: http://certs.trustcor.ca/sub/dv-ssl-rsa.der Signature algorithm SHA256withRSA Extended Validation No Certificate Transparency Yes (certificate) OCSP Must Staple No Revocation information CRL, OCSP CRL: http://crl.trustcor.ca/sub/dv-ssl-rsa-s-66.crl OCSP: http://ocsp.trustcor.ca Revocation status Validation error OCSP ERROR: Exception: connect timed out [http://ocsp.trustcor.ca] CRL ERROR: IOException occurred DNS CAA No (more info) Trusted Yes Mozilla Apple Android Java Windows Additional Certificates (if supplied) Certificates provided 4 (5277 bytes) Chain issues Contains anchor #2 Subject TrustCor DV SSL CA - G2 - RSA Fingerprint SHA256: beb51c8f452426b2b9e672f7dd1eea4b33d6c38f4ca2a96956ce24bd05b0c38d Pin SHA256: eS9Oc92+qoeyy7FaGbRe6FO/VTah35Lxm0PDdpsLdHc= Valid until Sun, 30 Dec 2029 22:59:59 UTC (expires in 8 years and 6 months) Key RSA 2048 bits (e 65537) Issuer TrustCor DV SSL CA - G2 Signature algorithm SHA256withRSA #3 Subject TrustCor DV SSL CA - G2 Fingerprint SHA256: f0b6b7598df2790471552632eba9cde6d349065fc6d665957f9eeef5a7bb24f2 Pin SHA256: joJVEgkWNcXOGzwqvqRUGUI1s5Dz+sm7yE2V6LjAa9A= Valid until Sun, 30 Dec 2029 23:59:59 UTC (expires in 8 years and 6 months) Key RSA 2048 bits (e 65537) Issuer TrustCor RootCert CA-1 Signature algorithm SHA256withRSA #4 Subject TrustCor RootCert CA-1 In trust store Fingerprint SHA256: d40e9c86cd8fe468c1776959f49ea774fa548684b6c406f3909261f4dce2575c Pin SHA256: 6of0Yt7v/713daoqS34Py5HCLu5t9p7ZAQDMxzsxFHY= Valid until Mon, 31 Dec 2029 17:23:16 UTC (expires in 8 years and 6 months) Key RSA 2048 bits (e 65537) Issuer TrustCor RootCert CA-1 Self-signed Signature algorithm SHA256withRSA Show Certification PathsCertification Paths Click here to expand Configuration Protocols TLS 1.3 No TLS 1.2 Yes TLS 1.1 No TLS 1.0 No SSL 3 No SSL 2 No Cipher Suites # TLS 1.2 (server has no preference) TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK 112 TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (0x41) WEAK 128 TLS_RSA_WITH_SEED_CBC_SHA (0x96) WEAK 128 TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) WEAK 128 TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) WEAK 128 TLS_RSA_WITH_RC4_128_MD5 (0x4) INSECURE 128 TLS_RSA_WITH_RC4_128_SHA (0x5) INSECURE 128 TLS_RSA_WITH_IDEA_CBC_SHA (0x7) WEAK 128 TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (0x84) WEAK 256 TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) WEAK 256 TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d) WEAK 256 Handshake Simulation Android 4.4.2 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Android 5.0.0 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_CBC_SHA No FS Android 6.0 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Android 7.0 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Android 8.0 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Android 8.1 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Android 9.0 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS BingPreview Jan 2015 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Chrome 49 / XP SP3 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Chrome 69 / Win 7 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Chrome 70 / Win 10 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Chrome 80 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS Firefox 31.3.0 ESR / Win 7 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_CBC_SHA No FS Firefox 47 / Win 7 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_CBC_SHA No FS Firefox 49 / XP SP3 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_CBC_SHA No FS Firefox 62 / Win 7 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_CBC_SHA No FS Firefox 73 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_CBC_SHA No FS Googlebot Feb 2018 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_GCM_SHA256 No FS IE 11 / Win 7 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS IE 11 / Win 8.1 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS IE 11 / Win Phone 8.1 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_128_CBC_SHA256 No FS IE 11 / Win Phone 8.1 Update R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS IE 11 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Edge 15 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Edge 16 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Edge 18 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Edge 13 / Win Phone 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Java 8u161 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_CBC_SHA256 No FS Java 11.0.3 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Java 12.0.1 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS OpenSSL 1.0.1l R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS OpenSSL 1.0.2s R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS OpenSSL 1.1.0k R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS OpenSSL 1.1.1c R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Safari 6 / iOS 6.0.1 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_CBC_SHA256 No FS Safari 7 / iOS 7.1 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_CBC_SHA256 No FS Safari 7 / OS X 10.9 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_CBC_SHA256 No FS Safari 8 / iOS 8.4 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_CBC_SHA256 No FS Safari 8 / OS X 10.10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_CBC_SHA256 No FS Safari 9 / iOS 9 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Safari 9 / OS X 10.11 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Safari 10 / iOS 10 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Safari 10 / OS X 10.12 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Safari 12.1.2 / MacOS 10.14.6 Beta R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Safari 12.1.1 / iOS 12.3.1 R RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS Apple ATS 9 / iOS 9 R Server sent fatal alert: handshake_failure Yahoo Slurp Jan 2015 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS YandexBot Jan 2015 RSA 2048 (SHA256) TLS 1.2 TLS_RSA_WITH_AES_256_GCM_SHA384 No FS # Not simulated clients (Protocol mismatch) Click here to expand (1) Clients that do not support Forward Secrecy (FS) are excluded when determining support for it. (2) No support for virtual SSL hosting (SNI). Connects to the default site if the server uses SNI. (3) Only first connection attempt simulated. Browsers sometimes retry with a lower protocol version. (R) Denotes a reference browser or client, with which we expect better effective security. (All) We use defaults, but some platforms do not use their best protocols and features (e.g., Java 6 & 7, older IE). (All) Certificate trust is not checked in handshake simulation, we only perform TLS handshake. Protocol Details DROWN No, server keys and hostname not seen elsewhere with SSLv2 (1) For a better understanding of this test, please read this longer explanation (2) Key usage data kindly provided by the Censys network search engine; original DROWN website here (3) Censys data is only indicative of possible key and certificate reuse; possibly out-of-date and not complete Secure Renegotiation Supported Secure Client-Initiated Renegotiation Yes Insecure Client-Initiated Renegotiation No BEAST attack Mitigated server-side (more info) POODLE (SSLv3) No, SSL 3 not supported (more info) POODLE (TLS) No (more info) Zombie POODLE No (more info) TLS 1.2 : 0x000a GOLDENDOODLE No (more info) TLS 1.2 : 0x000a OpenSSL 0-Length No (more info) TLS 1.2 : 0x000a Sleeping POODLE No (more info) TLS 1.2 : 0x000a Downgrade attack prevention Unknown (requires support for at least two protocols, excl. SSL2) SSL/TLS compression No RC4 Yes INSECURE (more info) Heartbeat (extension) Yes Heartbleed (vulnerability) No (more info) Ticketbleed (vulnerability) No (more info) OpenSSL CCS vuln. (CVE-2014-0224) No (more info) OpenSSL Padding Oracle vuln. (CVE-2016-2107) No (more info) ROBOT (vulnerability) No (more info) Forward Secrecy No WEAK (more info) ALPN No NPN No Session resumption (caching) Yes Session resumption (tickets) Yes OCSP stapling No Strict Transport Security (HSTS) No HSTS Preloading Not in: Chrome Edge Firefox IE Public Key Pinning (HPKP) No (more info) Public Key Pinning Report-Only No Public Key Pinning (Static) No (more info) Long handshake intolerance No TLS extension intolerance No TLS version intolerance No Incorrect SNI alerts No Uses common DH primes No, DHE suites not supported DH public server param (Ys) reuse No, DHE suites not supported ECDH public server param reuse No, ECDHE suites not supported Supported Named Groups - SSL 2 handshake compatibility No HTTP Requests 1 https://mondomaine.ly/ (HTTP/1.1 200 OK) Miscellaneous Test date Wed, 16 Jun 2021 16:55:27 UTC Test duration 199.208 seconds HTTP status code 200 HTTP server signature ?????? ???? ??????? Server hostname -
-
Dear Friends, I have been developing with unigui in C++builder Alexandria 11.1 in 64 bit mode using standalone server and when enable SSL it is giving me this exception Exception class EIdOSSLLoadingRootCertError with message First chance exception at $00007FFAC43D4F69. Exception class EIdOSSLLoadingRootCertError with message 'Could not load root certificate. error:00000000:lib(0):func(0):reason(0)'. Process xxxxxx.exe (6852) It won't happen if i compile in 32 bits. I am a registered UNIGUI user and the version that i am using is the 1.90.0.1560. it is happening in both debug and release configuratons. For testing i am using the self signed certificate following UNIGUI documentaton instructions. Also i am using the SSL dll that comes with the 1560 version. SSL config on ServerModule is SSL.Enabled = True SSL.SSLOptions.RootCertFile = 'root.pem' SSL.SSLOptions.CertFile = 'fl.cert.pem' SSL.SSLOptions.KeyFile = 'fl.key.pem' SSL.SSLOptions.Method = sslvTLSv1_2 SSL.SSLOptions.SSLVersions = [sslvTLSv1_2] SSL.SSLOptions.Mode = sslmUnassigned SSL.SSLOptions.VerifyMode = [] SSL.SSLOptions.VerifyDepth = 0 SSL.SSLPassword = 'fmsoft' SSL.SSLPort = 8080 I also tried SSL.Enabled = True SSL.SSLOptions.RootCertFile = 'root.pem' SSL.SSLOptions.CertFile = 'fl.cert.pem' SSL.SSLOptions.KeyFile = 'fl.key.pem' SSL.SSLOptions.Method = sslvSSLv3 SSL.SSLOptions.SSLVersions = [sslvSSLv3] SSL.SSLOptions.Mode = sslmUnassigned SSL.SSLOptions.VerifyMode = [] SSL.SSLOptions.VerifyDepth = 0 SSL.SSLPassword = 'fmsoft' SSL.SSLPort = 8080 The result is identical So i hope that someone can give me some light on this. Thanks in advance
-
FYI, this one works 'from your example code': cCIPHER_LIST_4: WideString = 'AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA'; (Stupid) question, I'm using a Self Signed certificate, could this be the issue?
-
Hello, From google : "When you use a self-signed SSL certificate, browsers cannot verify its authenticity. This means that the browser will detect an invalid SSL certificate and display a warning message to indicate the problem to users.15 déc. 2021" Perhaps in the past, it was validate and used for unigui demo, today it is nomore used. You have to buy a genium SSL from a known auhtority. You can try with somme cheaper SSL.
-
Hi Pals: I want to get rid of the secure message of the browers when my Customers use UniGui app inside a intranet. I use a self-signed certificate, but the browser complains because is not a know certificate authority. I use then the certificate of my Customer, but it not happy the browser. The certificate point to sebaotweb.sebaot.com. When use from internet works very fine. Internally are a transparent redirect on the dns to point sebaotweb.sebaot.com to the server using internal IP address. On the browser the url is the same if You are using from internet, but inside the net (intranet) the certificate is "insecure". Anybody knows how i can handle this problem? Thanks for all and Best Regards
-
Hello, Please provide more information. What certificate are you using? Self-signed?
-
Oh yes , i'm aware of that. If i compile the code in 32 bits then it works with both a self signed and a godaddy's certificate. But in 64 bits it doesn't work. it is giving the error i start this thread with. So any suggestions will be appreciated! Thanks in advance
-
Turns out that perhaps you could make a self signed certificate to avoid the pop-up message: Will try tomorrow. Lost a lot of time looking for a solution. Such information is not very clear in their website. Not even clear if self-signed certificates works or just trusted by a secure entities to a website only . https://qz.io/wiki/signing-messages Not verfy clear and even the presenter make some mistakes. Best source is this link below: https://ijustlearnedsomethingnewtoday.blogspot.com/2017/04/using-self-signed-certificates-with-qz.html I will keep you guys posted if it worked.